Probing Slack Workspaces for Authentication Information and other Treats

What Slack gives away for free
When you send a simple HTTP GET request (without any authentication) to a Slack Workspace URL, you get a HTML response with some Javascript, as you would probably expect. However, In those Javascript blocks is some interesting information:

In particular, one of the scripts has an attribute, data-props, that contains information on the workspace you are contacting; name, ID and whether it is a paid workspace etc. It also contains some important authentication information, such as approved domains, SSO status and whether two-factor authentication is required.
Remember, this information comes from an unauthenticated request, all you need to know is the domain of the workspace you are targeting.
Slack Watchman ‘unauthenticated probe’
I’ve added a new ‘unauthenticated probe’ option In Slack Watchman version 4.1.2, which makes the task of enumerating a workspace simple. You don’t need a token, all you need to know is the workspace URL.
Lets run an example probe on the Slack workspace that SpecterOps run for Bloodhound (for no other reason than its a good example); https://bloodhoundhq.slack.com:
slack-watchman --probe https://bloodhoundhq.slack.com 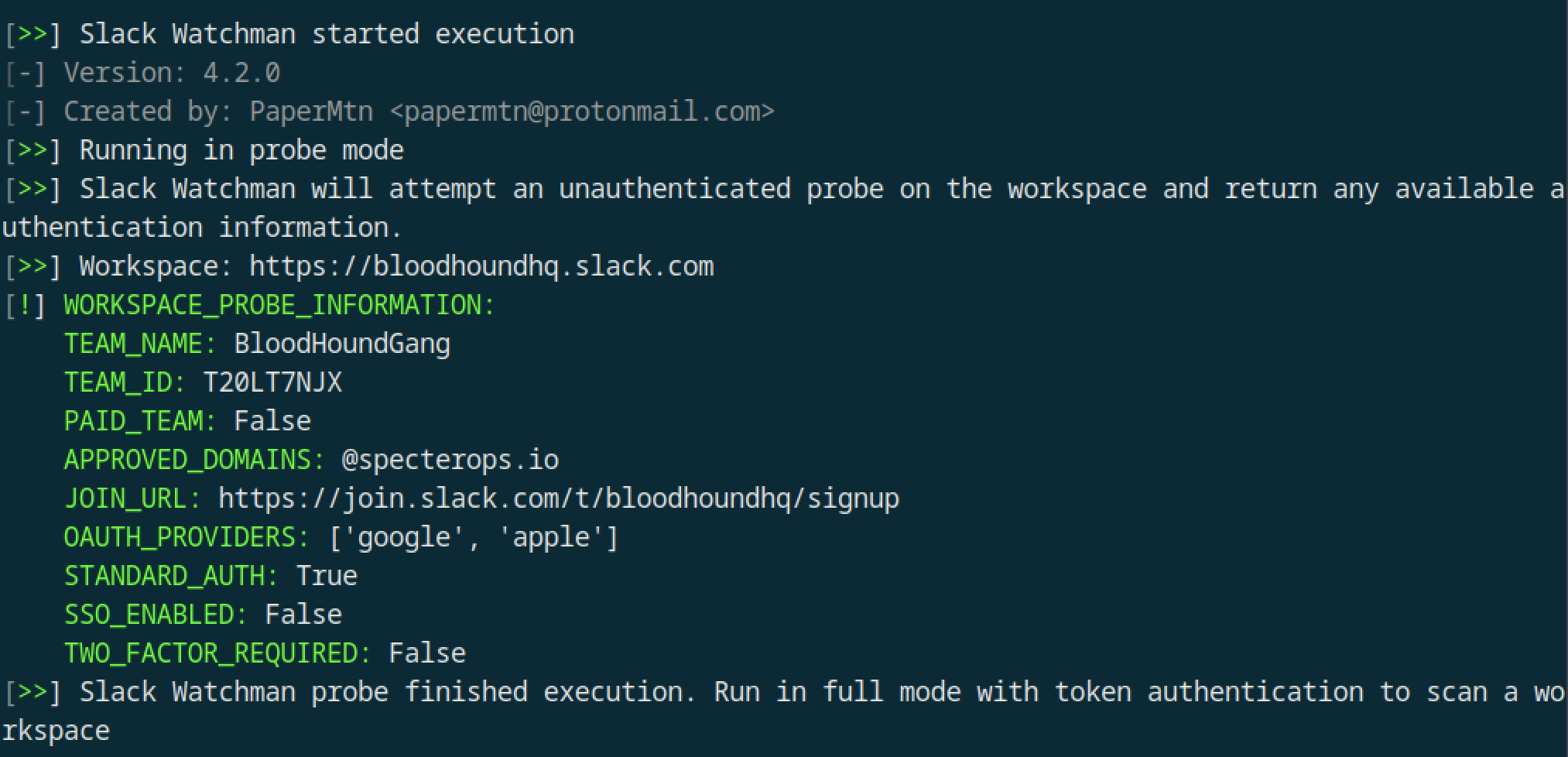
Slack Watchman has given us some interesting information:
- Two-factor auth is not enforced on users
- SSO is not enabled
- OAuth is enabled with Google and Apple
- The domain
specterops.iois automatically approved to create accounts (we’ll get into this later).
The real world implications of this
Red teams and blue teams can make use of this information. A red team can learn from this whether a target workspace has 2FA enforced, whether they use SSO or standard auth. You can also get the internal name and Slack ID of the workspace. This may help you with social engineering to get access.
For blue teams, especially those without direct access to a Slack workspace's settings, you can use this to learn about the authentication settings for the workspace, and any potential weaknesses.
Approved Domains
Of particular importance is the APPROVED_DOMAINS value. Any domains here are automatically provisioned for creating accounts in the workspace, without needing an invitation from a current member or approval from an admin. This means, if you have an email account for this domain, you can create an account for yourself for the Slack workspace using the JOIN_URL that Slack Watchman returns.
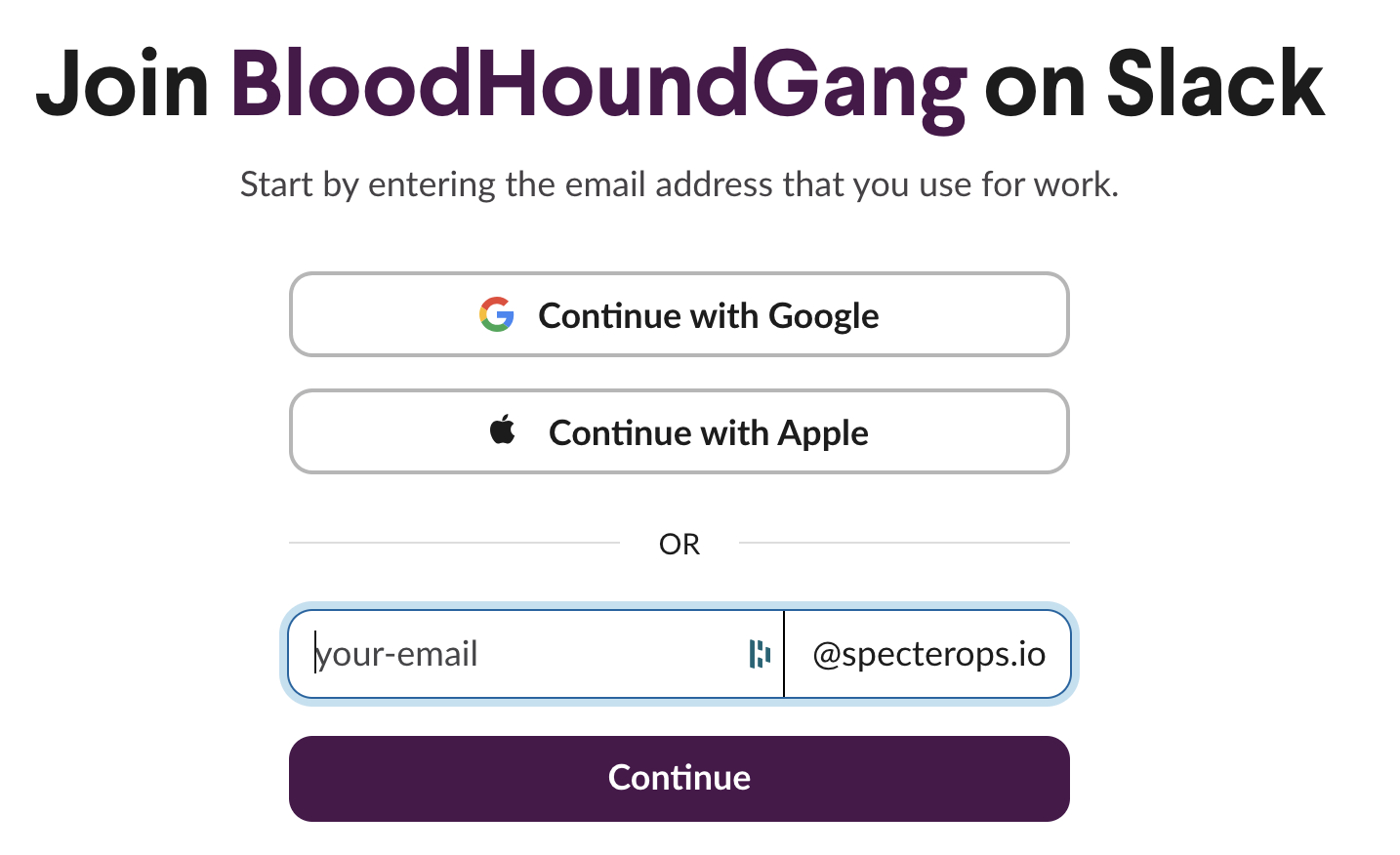
There are two situations where this may be worth keeping an eye on:
1. An old domain, that is no longer owned by the organisation, is still approved
If this domain is available for purchase, you could aquire the domain and gain access to the workspace via an email account using that domain:
- Blue teams, you should be on the lookout for this and make sure no stale domains are approved for access to your Slack workspace.
- Red teams, you should be on the lookout for this as a way of gaining access to workspaces.
2. A domain from free mail providers
There is the chance that a free mail provider may be configured with access to a workspace. Luckily (from a defensive point of view at least), Slack won’t allow you to use a lot of the common ones, such as Gmail:
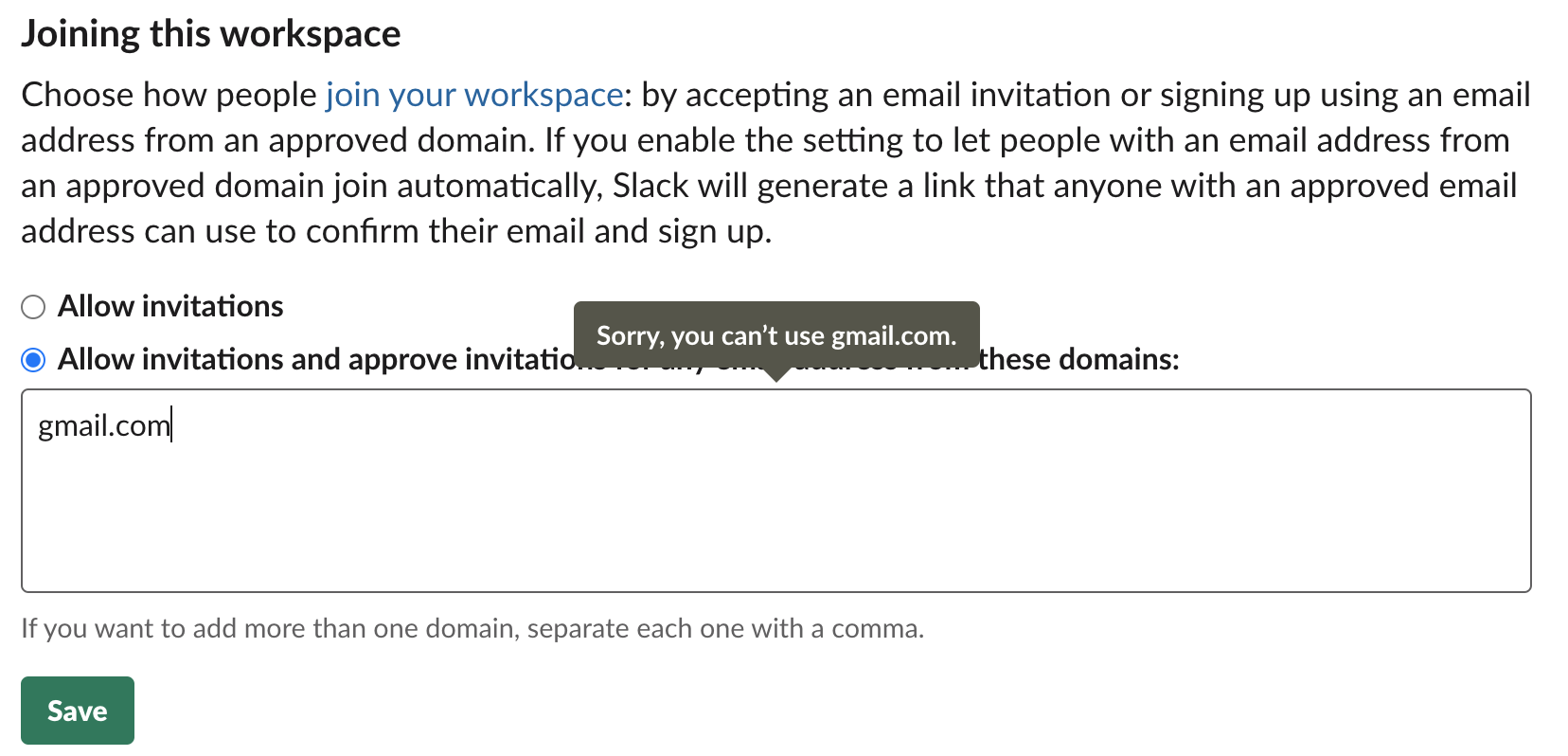
By manually checking a few common free email providers, i’ve found these are some domains that Slack doesn’t let you use:
gmail.comoutlook.com,hotmail.com,live.com,msn.comyahoo.comicloud.comaol.comprotonmail.comzoho.comgmx.commail.comyandex.com,yandex.rututanota.com
However, a few i’ve found that are allowed:
zoho.commail.comtutanota.com
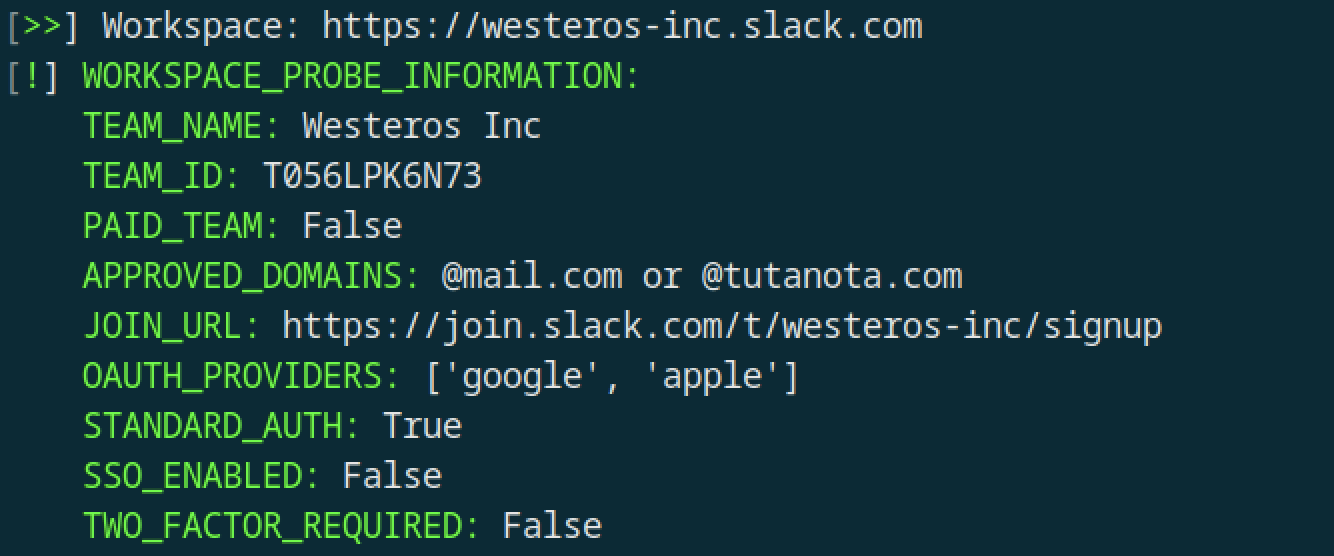
- Blue teams, you will want to remove any domains of common email providers from being approved in your workspace. You can do this following the guide here.
- Red teams, if you find a common email provider domain in the approved list, it’s open season…
Summary
Slack Watchman can now gather even more information from Slack Workspaces, without any need for authentication. You can use this information for your offensive engagements, or to make sure your Slack resources are as secure as possible.
If you’ve not used it before, check out the GitHub repository for Slack Watchman, and give it a go to detect secrets and sensitive information being shared in Slack Workspaces.



